The scale of cybersecurity fraud is staggering and costs businesses and individuals trillions of dollars every year. According to Brush Cyber CEO Doug Brush, this criminal industry is efficient and well-funded.
“If you look at cybercrime as a whole, some estimates put it at a $13 trillion economy,” he explains. “That makes it the third largest economy in the world after the U.S. and China.”
Private foundations are particularly prone to targeted attacks as criminals perform intense reconnaissance on organizations.
Doug's findings indicate that attackers meticulously research their targets, often seeking access to donor and funding lists. These lists are a goldmine for committing wire fraud and identity theft.
Private foundations must be vigilant, recognize the specific cyber threats they face and establish a comprehensive cybersecurity risk management plan to protect their most sensitive and valuable information.
TYPES OF CYBERSECURITY ATTACKS
Private foundations are particularly susceptible to two primary cybersecurity threats: compromised email accounts (business email compromise or BEC) and ransomware.
“Private foundations have financial assets that are at risk,” shares GHJ Audit and Assurance Amy Eybsen. “Financial transactions are at high risk, particularly where wire transfers are involved.”
Criminals use stolen email credentials to gain access to email systems and then monitor traffic for specific keywords, such as “transfer money” or “wire transfer.” Then, they slip into the email threads to send an email with new wire transfer credentials to divert funds from the intended recipient to their account. After 72 hours, the funds are often unrecoverable and both parties in the email exchange and wire transfer become unaware victims until it is too late.
“Email is often the weakest link. The easiest prevention is to verify wire transfer information, even if you know the other party,” Doug says. “People do not pick up the phone, call a known good number and ask the other party if the banking information makes sense. This would stop most fraud.”
Ransomware refers to information essentially held hostage by a threat actor and can only be made accessible again via decryption keys the threat actors “sell” back to the organization to restore data. Doug says such an attack can shut down an entire organization for days or weeks.
Additionally, the threat actor often steals sensitive data and threatens to publish it on the Dark Web if the organization does not pay them ransom.
This ploy is typically quite sophisticated. The threat actor has done enough research to know an organization's financials, such as their cybersecurity insurance limits or profit-and-loss statements. This makes it easy to request a specific amount of money that does not cause too much friction within the private foundation.
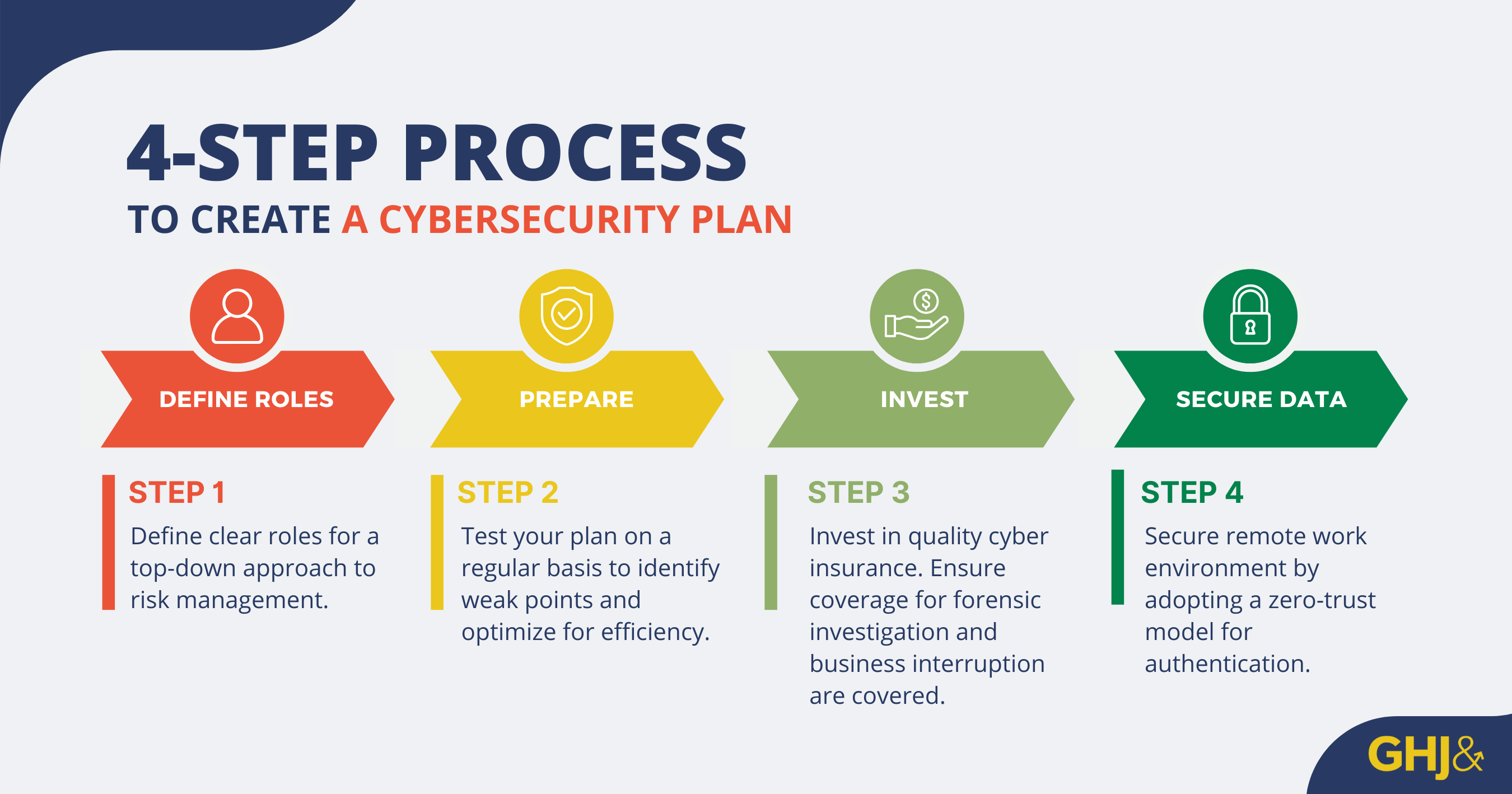
HOW TO CREATE A CYBERSECURITY RISK MANAGEMENT PLAN
A top-down strategy can prevent and mitigate both types of cybersecurity attacks. While Doug gives specific recommendations on what to include in your risk management plans, these should be considered a starting point for creating a plan.
“Organizations should not wait for perfection,” Doug says. “Any formal policy is better than none at all.”
In addition to the loss of funds or sensitive data, there could also be litigation or regulatory issues that may be incurred. Colin Nierenberg, an Audit Manager at GHJ who works with several nonprofit clients in managing their risks and analyzing data, reiterates the need for a clear chain of responsibility and response.
“We have seen issues with business email compromise and wire fraud in the private foundation community,” Colin shares. “Executives are worried about termination if a compromise takes place, but this fear can be alleviated by creating proper plans and protocols.”
The foundation's executive leadership team can start the risk management process by discussing two essential questions:
- What is the minimal effective dose you need?
- How do you get that minimal effective dose in a short amount of time and defend it in case of an investigation?
The best place for foundations to start, according to Doug, is to look at how financial transactions occur within the organization and build resiliency around those processes. Consider the following steps when creating a risk management plan.
WHAT TO DO IN RESPONSE TO A CYBERSECURITY BREACH
If a cybersecurity issue does arise, private foundations should take action without panicking. They should stay calm and execute their incident response plan. That is why it is so important to plan ahead rather than work reactively in a time of stress. Prepared foundations already have the exact steps that need to be executed.
Even with a cybersecurity response plan in place, consider hiring a law firm specialized in cybersecurity if a breach occurs. Avoid relying on the Foundation's general counsel and opt for an expert from the beginning.
A law firm with expertise in data breaches helps navigate legal and regulatory issues. There are multiple jurisdictions (including states and other countries) that each have their own requirements for reporting data loss.
Working with a professional lawyer also gives a private foundation access to forensic resources. This helps to avoid mistakenly erasing information that is needed for the investigation.
RISK MANAGEMENT POLICIES TO CONSIDER
There are a few different policies and initiatives that foundation board members and executives can create to lower the threat of cybersecurity attacks. Start with a wire transfer policy that defines when verbal confirmation is required in response to changes in payment information.
Next, craft record-keeping policies that define the following details about the foundation's data:
- The type of information collected
- How long it is kept
- How data is collected
- Who has access
Because data storage costs are so low, it can be tempting to keep data indefinitely. However, Doug recommends letting outdated data expire.
“The value of data goes down over time, but the risk remains high,” he explains. “You cannot get sued or breached over deleted data you no longer have a business or regulatory need to possess.”
Private foundations should also incorporate ongoing employee training efforts. Educate executives and C-suite of the unique risks they face as organizational leaders. They are at risk of being targeted based on information online, including personal details about their lives. This targeted type of reconnaissance and targeted attack is called “whaling.”
The next step is raising employee awareness. Doug recommends that messaging about cybersecurity come directly from C-suite executives in their own words.
“Do not make employees feel like they are going to get in trouble,” he says. “Instead, get them excited to help protect the organization.”
Finally, create a policy to evaluate the risks of any new initiatives before they launch. There may be increased access to sensitive information when working with multiple departments or external vendors. By incorporating threat prevention measures, foundations can mitigate those risks before they occur.
| GHJ’s Risk Management for Private Foundations Series: Navigating Challenges and Seizing Opportunities dives deep into the risks that private foundations face and offers practical solutions across a spectrum of areas including automation, cybersecurity and new giving strategies. Gain insights into implementing new ideas, ensuring compliance and exploring innovative partnerships to enhance impact. Learn more. |