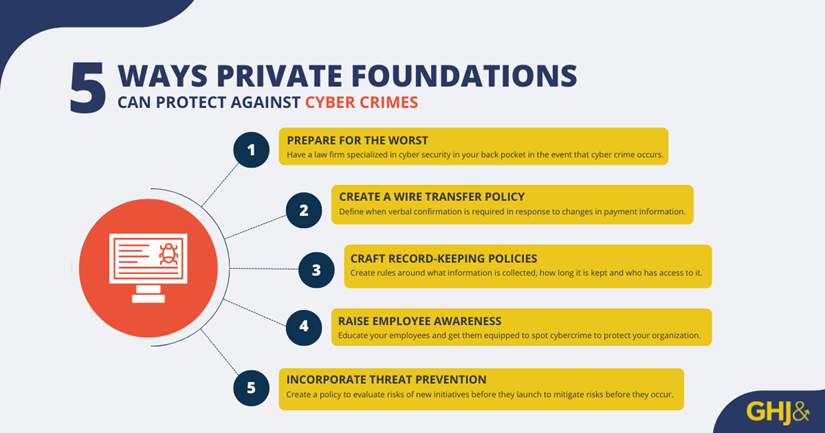
How can organizations ensure they are prepared for potential cybersecurity threats? There are several steps that can be taken.
STEP 1: UTILIZE DIFFERENT ROLES IN THE FOUNDATION FOR A TOP-DOWN APPROACH
Every department should have a clear understanding of its responsibilities. But ultimately, the risk management strategy must come from the executive team. Their role is to provide each stakeholder with an action plan for what to do in the event of a cybersecurity attack.
- Executives: Create the policies and provide a supportive environment for departments and individual employees to execute these policies. This includes gating conditions to pause transactions when suspicious activities occur.
- IT: Craft approved protocol for executives to follow in the event of a breach. This is vital so that no one deletes important data out of fear.
- Public Relations: Create a communications plan in advance that outlines how to tell relevant stakeholders about a security breach. This allows the foundation to be proactive rather than reactive during a breach.
- All employees: Everyone should know the protocol for gating conditions if any suspicious activity takes place. An example protocol would be if an employee is told at any point to change banking or wire information during a transaction, they must halt the transaction immediately and call a designated executive.
STEP 2: REGULARLY TEST YOUR PLAN
Testing is a key component of any foundation's risk management protocol. Perform regular tabletop exercises that include executives, board members, the IT department and the Public Relations team.
Also, have a phone tree in place. An attack can happen outside of business hours, so it is important to formalize the chain of command and how the response team will be reached.
Finally, validate what works in the plan and what needs to be changed. Foundations should gather feedback from each department after testing and incorporate those updates into their cybersecurity protocol.
STEP 3: PURCHASE A QUALITY CYBER INSURANCE POLICY
Cyber insurance is becoming more common among private foundations as a way to financially protect themselves against these risks. But not all policies are created equally.
When private foundations evaluate options, they should compare policy coverage and limits. Check for coverage of likely expenses that come with a cyberattack, such as forensic investigation, litigation and regulatory penalties and business interruption.
Brush Cyber Owner Doug Brush recommends using a broker to help choose your policy.
“They get paid for placing policies and renewals, so they want to make sure you are not dropped if you have an event,” he said.
It is in their best interest to ensure the foundation has the right coverage for their specific needs.
Also, remember that the size of a foundation's ideal policy is not necessarily tied to assets or revenue, but the number of data records with sensitive information.
STEP 4: REDUCE THE RISKS OF REMOTE WORK
Many private foundations shifted to a full or partial remote work model as a result of the pandemic.
“Many of our private foundation clients do not even have offices anymore,” notes GHJ Managing Director Amy Eybsen. “But this increases risk as many employees are using personal cell phones and working on home Wi-Fi networks.”
To mitigate these external risks, Doug recommends taking two more steps to keep ransomware attacks at bay.
The first is to implement a zero-trust model, which never presumes user identity or network security. It requires frequent reauthentication to make sure all devices are secure with the correct user logging on.
Next, foundations can integrate an analytics program that shuts down access if there is suspicious behavior. Then it sends a notification to the right people in the foundation to take the next steps.
"Although it can be frustrating for workers who temporarily lose access, the zero-trust model is a preventative measure to make sure it is an authenticated session," Doug explained.
| GHJ’s Risk Management for Private Foundations Series: Navigating Challenges and Seizing Opportunities dives deep into the risks that private foundations face and offers practical solutions across a spectrum of areas including automation, cybersecurity and new giving strategies. Gain insights into implementing new ideas, ensuring compliance and exploring innovative partnerships to enhance impact. Learn more. |